
Session Hijacking
October 03, 2022
Since HTTP is stateless, application developers had to create a way to track the state between multiple connections from the same user. This ensures no authentication request for each user's click on a web application or website. A session is a communication process between a user and a server during a single connection. It is created on the server when a user logs in to a website or an application. It allows the state to be maintained for other requests from the same user. Applications use them to store parameters that are important to the user. A session is kept "alive" on the server as long as the user is logged in and ends if the user logs out or after a certain period of inactivity. When the session is destroyed, the user's data is also deleted from the allocated memory space.
A session identifier is an identification string (usually a long random alphanumeric string) transmitted between the client and the server. The system can generally store such identifiers in cookies, URLs, and hidden fields in web pages. In addition to their usefulness, several security issues are associated with them. Because websites often use algorithms based on easily predictable variables, such as time or IP address, to generate session identifiers, this makes them predictable. In addition, when there is no encryption (usually SSL), they are transmitted in the clear and can be intercepted.
What is Session Hijacking?
Session Hijacking is a process where an attacker can compromise a user, which can involve identity theft. Once a user begins a session, such as logging into a banking site, an attacker can hijack the user. To do this, the hacker needs to get the user's cookies. Browser or web application sessions are most often targets for such actions.
How is a session hijacked?
There are several options for hijacking a user's session, depending on the attacker's position and attack vector. Here are the main methods of Session Hijacking:
- Cross-site scripting (XSS): attackers exploit vulnerabilities in servers or applications to inject client-side Java scripts into users' Web pages. Such a trick forces your browser to execute arbitrary code when the compromised page loads. Suppose the server does not set HTTPOnly in the session cookie. In that case, the injected scripts can access your session key, giving attackers the information they need to hijack your session.
- Session sidejacking: using packet hijacking, an attacker can monitor network traffic and intercept the user's session cookie after authenticating. Suppose a website chooses the low-cost method of using SSL/TLS encryption only for its login pages. Then, an attacker can use the session key he obtains from packet hijacking to capture the user's session and impersonate it to perform actions in the web application. This typically occurs at unsecured Wi-Fi hotspots, allowing the attacker to access the network, control traffic, and set up their hotspots to perform the attack.
- Session fixation: attackers provide a session key and spoof the user to access the vulnerable server.
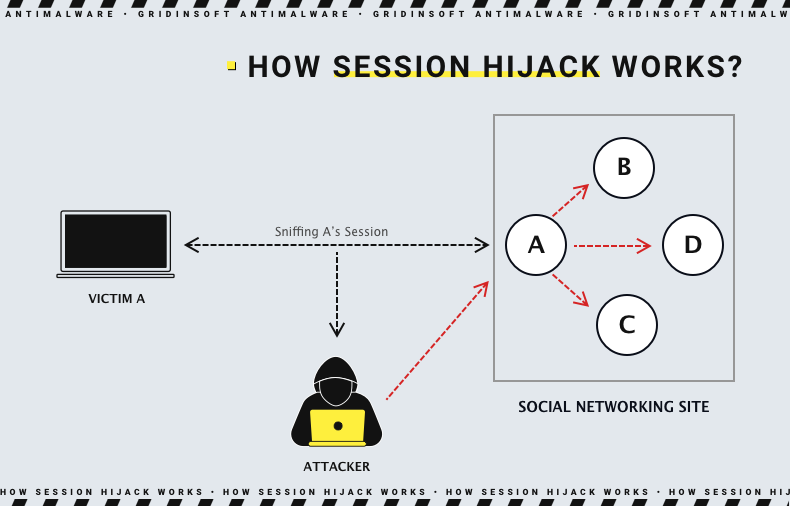
Because the protocol has no state preservation, Session Hijacking is a threat. Additionally, because of their limitations, protocols are vulnerable to attack.
What do attackers get from Session Hijacking?
If cybercriminals manage to hijack a session, they can do almost anything a legitimate user can do during an active session. The most severe cases include:
- Transferring money from a user's bank account. After an interception of the session with the online banking site, the attacker can do whatever the regular user does. However, the sole action will likely be draining the user’s accounts to zero.
- Managing the user’s account in social media. This threat is perilous for influencers with a wide audience on YouTube, Twitter, Facebook, or any other popular site. Hackers aim to use your name to spread malicious content like fake giveaways or fraudulent ads, and they will do this as soon as they get access to your account.
- Buying goods from online stores. Some online retailers offer to link the bank card to the account on their website to make a one-click purchase. That is convenient not only for you but also for fraudsters who manage to hijack your browser session with an online store.
- Accessing personally identifiable information (PII) to steal personal information. Any account contains the personal details, and some even provide enough data for a detailed dossier. Getting it means obtaining a great basis for spear phishing and making it possible to steal your identity for malicious purposes.
- Stealing data from company systems. Companies also use sessions to manage the employees’ connections to corporate resources. Hijacking is an easy way to reach confidential information and may be performed to gain initial access to the corporate network.
How to Prevent Session Hijacking?
To protect yourself from being hacked during a session, you need to harden the mechanisms in your web applications. This can be done through session management. Let's check out some tips that help reduce the risk of session hijacking:
Use reliable security technologies for data transfer
HTTPS connection is a great way to secure your session. Using HTTPS provides SSL/TLS encryption on all session traffic. Even if hackers monitored the victim's traffic, they would not be able to intercept the session ID in the clear. It is recommended to use HSTS (HTTP Strict Transport Security) to ensure full encryption.
HTTPOnly is the other HTTPS-based way of securing the session between you and the server. Setting the HTTPOnly attribute prevents access to stored cookies from client-side scripts. This can prevent attackers from deploying XSS attacks by injecting JavaScript into the browser.
Keep the things tight and secured
Using the antivirus with internet monitoring functions will likely weed out the places you can be exposed to the session hijack. Install reliable software that can easily detect viruses and protect you from malware (including malware used by attackers to hijack your session). Also, keep your systems up to date. Updates can contain critical security patches, so don't neglect them. It's best to set up automatic updates on all your devices.
It is also recommended to keep network security in mind. It is recommended to avoid using public Wi-Fi. Public networks are rarely protected in a diligent manner and can easily be exploited by crooks. Using the network secured with WPA technology is recommended to retain the security level. Another great solution to prevent session hijack by encrypting the traffic is to use VPN. Most of the solutions on the market offer traffic encryption.
Session security on the endpoint
To ensure sufficient security, website operators can use web frameworks instead of inventing their session management systems. However, the latter is important as well. A session key is a cryptographic confirmation of the reliability of the user's connection to the server. It is recommended to re-generate session keys after their initial authentication. This makes the session ID retrieved by attackers useless because it loses relevance immediately after authentication.
Identity verification is an important part of cybersecurity. Perform additional proof of the user's identity outside the session key. This includes verifying the user's standard IP address or application usage patterns. Hackers can barely spoof these data. Hence such a multifactor authentication can make sense.
Role of Encryption
Organizations can use specific encryption methods to protect a user's session from hacking. These encryptions are required to protect your consumers' sessions and take the form of certificates. SSL (Secure Sockets Layer) is a default technology for securing Internet connections and protecting sensitive data transmitted between two systems. It prevents criminals from reading and changing any information transmitted, including personal data. Some resources offer TLS (Transport Layer Security) - an updated, more secure SSL version.
Frequently Asked Questions
Analysts name 3 different types of session hijacking - active, passive and hybrid. In active, fraudsters take advantage of your connection to the server by intercepting it forcibly. It is usually achievable when one of the sides is compromised, or there is a connection issue known to a fraudster.
Passive hijacking supposes the session interception similar to the active one. However, instead of forced connection interruption, hackers just monitor the traffic waiting for the session authenticator to appear among the packets. Again, that requires an unencrypted protection or a spoofed public key.
Hybrid session hijacking conjoin both of the mentioned ways, when the hacker just spectates the connection unless the issue is uncovered. Then, it starts acting like in the case of an active hijack - exploits the issue to gain access to the session.
Session hijacking and IP spoofing are similar in effect to its victim - in both cases, you lose your personal information. The key difference is in the approach chosen by cybercriminals, and the scale of what is happening. IP spoofing is a method of a public key hijack - the protection key that is issued each time you are establishing the connection to a server. It is needed to protect the data you exchange with this server. Having this key, fraudsters can read the data packets you send to and receive from the server. Hence, your queries, chats and possibly passwords can be compromised.
Session hijacking is an action that aims more precisely on your account. Having your session hijacked means instant transfer of the control over the account to hackers, without the need for them to dig into the leaked data packets. In some cases, crooks may use IP spoofing as a precursor to a session hijacking - by obtaining the key to your data, they will be able to get the session info, and thus use it.